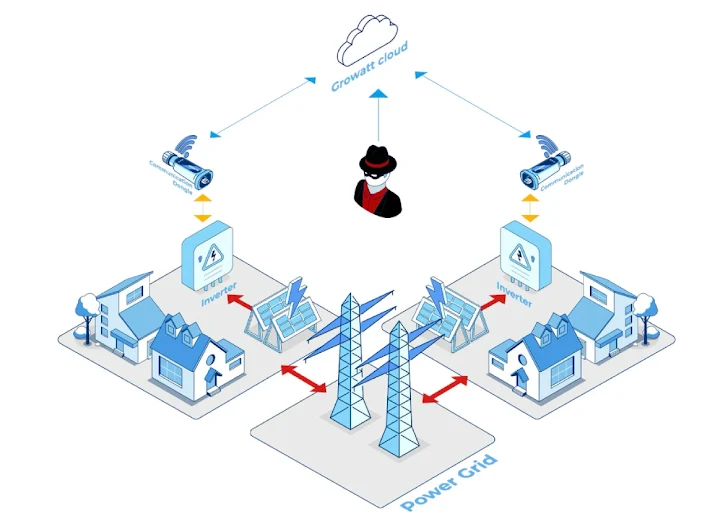
Have you ever wondered how secure the devices powering your sustainable energy solutions are? It’s a question more of us should be asking, especially in light of some startling new revelations about vulnerabilities in solar inverters from some of the most popular brands: Sungrow, Growatt, and SMA. With sustainability becoming more central to how we live, any potential chink in the armor of solar technology should naturally pique our concern. Let’s break down exactly what was uncovered, why it matters, and what steps are being taken to safeguard the grid.
Understanding Solar Inverters and Their Role
Before we put on our virtual detective hats, it’s important to understand what a solar inverter is and why it’s crucial. Simply put, solar inverters are devices that convert the DC electricity generated by solar panels into AC electricity, which can then power our homes and businesses. They’re like the translators in the grand solar production line, ensuring that the energy harnessed from the sun can seamlessly be integrated into our daily lives.
Given their pivotal role, any vulnerabilities in these devices could potentially disrupt not just single homes, but entire power systems, making them attractive targets for cyber-attacks.
Enter Forescout: Lifting the Lid on Vulnerabilities
A team of cybersecurity researchers at Forescout Vedere Labs chose to stick their investigative noses into the businesses of three major solar inverter manufacturers: Sungrow, Growatt, and SMA. What they discovered were 46 critical security flaws—collectively codenamed SUN:DOWN—that could potentially allow nefarious actors to seize control of these devices and execute code remotely. The implications of these flaws are severe, given their potential to disrupt entire electrical grids.
What Exactly Did They Find?
Let’s get into the nitty-gritty of the vulnerabilities that were uncovered. Some of the most severe include:
-
Remote Code Execution (RCE) Vulnerabilities: Attackers could upload specific types of files to be executed by the web servers of these inverters, potentially leading to complete device takeover.
-
Username Enumeration and Account Takeover: Through exposed endpoints, attackers could perform username enumeration, hijack accounts by resetting passwords, and take over control of the devices.
-
Data Breaches: Sensitive data such as energy consumption information and device serial numbers could be accessed by unauthorized individuals, leading to potential breaches in user privacy and security.
-
Insecure Data Transmission: In the case of Sungrow, insecure encryption methods meant that attackers could intercept and decrypt communications, leading to potential data leaks or manipulations.
Table of Notable Vulnerabilities
| Manufacturer | Vulnerability Type | Potential Impact |
|---|---|---|
| SMA | RCE via .aspx files | Full device takeover |
| Growatt | Exposed API Endpoint | Username enumeration and account hijack |
| Sungrow | Weak AES Encryption | Data interception and exposure |
The Potential Threat Landscape
You might be wondering just how risky these vulnerabilities are, in situational terms. Imagine a scenario where a bad actor, upon exploiting these vulnerabilities, could control a significant number of inverters. With this control, they could potentially manipulate the amount of energy directed to the grid, affecting energy production and stability. An orchestrated attack using hijacked inverters could effectively act as a botnet, causing grid disruptions or even blackouts. These infiltrations represent not just a breach in digital security, but a tangible threat to our day-to-day living.
Real-World Impact Possibilities
The impact of these vulnerabilities extends beyond just the possibility of power disruption:
- Economic Consequences: Grid downtime can result in significant losses, affecting businesses, services, and individual consumers.
- Public Safety: In sensitive locations like hospitals, power stability can be a matter of life and death.
- Confidence in Renewable Energy Solutions: Widespread vulnerabilities can shake public confidence in solar and other renewable solutions.
How Are Manufacturers Responding?
Upon discovering these vulnerabilities, the manufacturers were informed through a process known as responsible disclosure. This practice ensures that the tech companies are given a chance to fix issues before the information becomes public. All the vendors have rolled out updates addressing these flaws, reinforcing the security of their systems.
Response Strategy: Patch and Protect
Manufacturers have employed several strategies to address the identified issues:
- Deployment of Software Patches: Quickly rolled out to fortify systems and block exploits.
- Enhanced Security Protocols: Improvement in how data is encrypted and communicated across networks.
- User Education: Informing consumers about the updates and ensuring they’re applied correctly.
Looking Forward: Strengthening Cybersecurity for Solar Tech
Security in our digital age is a constantly moving target. As we rely increasingly on interconnected systems, particularly in renewable energy, the need to ensure robust defenses becomes ever more crucial.
Recommendations for Users and Industry Players
- Conduct Regular Security Assessments: Identify potential vulnerabilities early and act on fixing them.
- Enforce Strong Security Measures: Implement strict security requirements when acquiring and installing solar equipment.
- Maintain Network Visibility: Having a clear view of network activity helps in identifying anomalous or unauthorized actions.
Industry-Wide Measures
- Standardized Security Compliance: Adoption of industry-wide security standards to ensure consistency across all manufacturers.
- Collaborative Security Efforts: Encourage cooperation among manufacturers to share threat intelligence and improve overall security posture.
Final Thoughts
The discovery of vulnerabilities in solar inverters by Forescout Vedere Labs underscores a critical truth in today’s technology landscape: as we rush forward in the quest for sustainable solutions, we must equally prioritize security. The green energy wave is nothing short of revolutionary, but like all revolutions, it must be protected against counteractive forces.
By staying vigilant and proactive, both manufacturers and consumers can ensure that the path to a sustainable future remains bright and uninterrupted—secure in the knowledge that our renewable infrastructure is as resilient as it is innovative.
So, what can you do? Stay informed, keep abreast of updates from your equipment providers, and know how to apply those lessons to bolster your own energy security. That’s how we keep the lights on, now and in the coming years.